Salient designed a powerful hybrid cloud solution. By creating a smooth path for cloud adoption, Salient minimizes disruptions and ensures a seamless transition, aligning digital transformation and cloud initiatives with video security infrastructure. When remote access is powered by the cloud, it becomes more scalable, secure, and easier to manage. Salient’s hybrid cloud approach delivers exactly that—combining the dependability of on-premises storage with the flexibility of cloud-based access, extended storage, and built-in disaster recovery. The result: stronger security, simplified operations, and a faster path to digital transformation.
Easy to Adopt
- Salient Cloud Services is integrated with CompleteView and does not change how you deploy your VMS.
- Register at no cost to seamlessly view your deployment assets from a web dashboard.
- Salient’s cloud service does not disrupt the functioning of your VMS, making it easy to evaluate and adopt cloud with no risk to your existing operations.
Simple and Secure Remote Access
- Salient automatically configures an encrypted connection to enable remote access.
- No changes to security configurations, VPN settings, or firewalls are required.
- With a few mouse clicks, you can remotely monitor, manage, and maintain your deployment while allowing your users to remotely access video anytime, anywhere, on any device.
- It is as plug-and-play as we can make it.
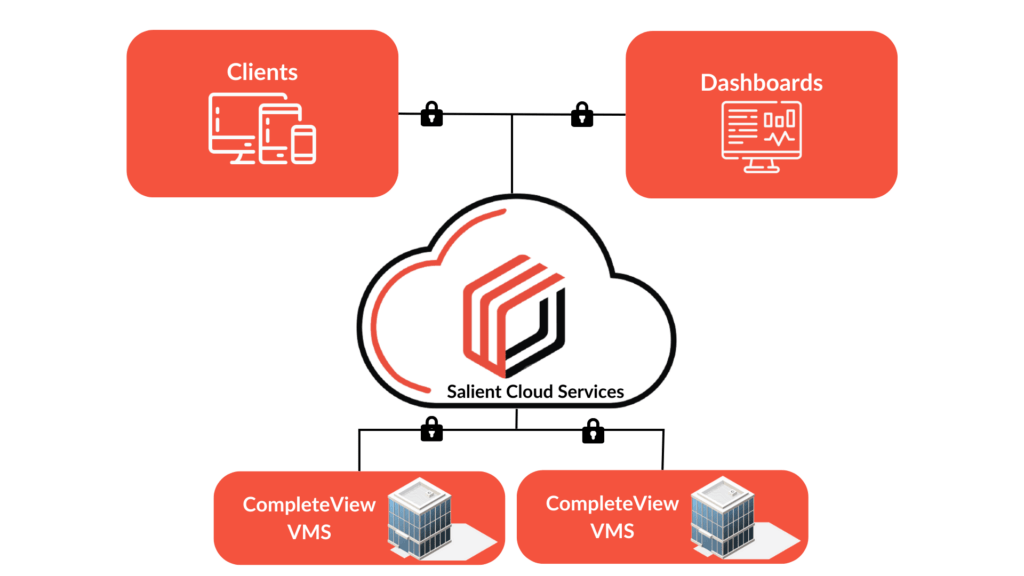
Connect your CompleteView deployment to Salient Cloud Services to unlock operational efficiency and value from your video management system
Maintain Control and Ownership
- Cloud Services puts you in complete control of your deployments and who has access to your video data.
- Centralized management remains on-site.
- For an added layer of security, we do not store user credentials or video in our cloud.
- It is easy to evaluate and adopt Salient Cloud Services without disrupting your service or operations.
Centrally manage users across a deployment
Remotely review health of cameras, storage, and recorders
Instantly access new cloud features and seamlessly deploy updates to on-premises components
Reduce downtime by troubleshooting issues remotely
Simple and secure remote access on any device
No need to make any firewall changes or involve IT
Subscription Benefits
Easy, secure remote access for customers and integrators
- Use existing CompleteView clients
- Secure connectivity with end-to-end encryption
